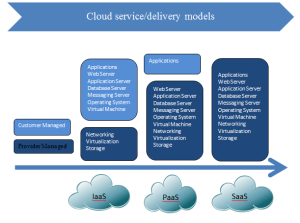
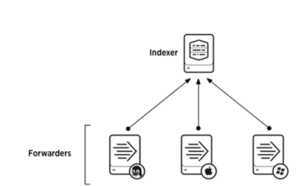
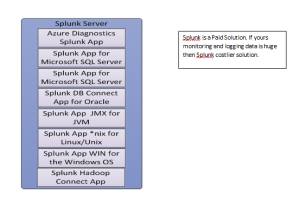
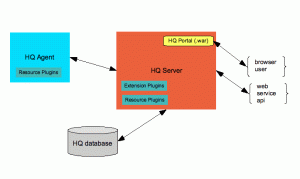
Follow following steps to connect Kerberosed Hive form Local Windows desktop/laptop:
- Install MIT Kerberos Distribution software from “http://web.mit.edu/kerberos/dist/”
- Configure winutils.exe for Hadoop connection from “https://github.com/steveloughran/winutils/tree/master/hadoop-2.7.1/bin”
- Set up the Kerberos configuration file in the default location.
- Obtain a krb5.conf configuration file from your Kerberos cluster default location in Hadoop cluster (/etc/krb5.conf).
- The default location is C:\ProgramData\MIT\Kerberos5. This directory may be hidden by the Windows operating system. So enable hidden file viewing..
- Rename the configuration file from krb5.conf to krb5.ini.
- Copy krb5.ini to the default location and overwrite the empty sample file.
- Set up the Kerberos credential cache file.
- Create a writable directory. For example, C:\temp
- Create environment variable KRB5CCNAME and Enter variable value: <writable directory from step 1>\krb5cache. For example, C:\temp\krb5cache
- Copy winutils to local env as bin folder containing winutils.exe sample: C:\winutils\bin\winutils.exe
- Gather and set below information in the sample or wm configuration files:
userPrincipalName = “user@REALAM.COM”;
keytabPath = “C:/users/user/user.keytab”;
kdcHost = “kdc.host.com”;
releam = “REALAM.COM”;
winUtilHome = “C:\\winutils\\”;
#####################################################################
Code Sample :
import java.sql.Connection;
import java.sql.DriverManager;
import java.sql.ResultSet;
import java.sql.ResultSetMetaData;
import java.sql.SQLException;
import java.sql.Statement;
import org.apache.hadoop.conf.Configuration;
import org.apache.hadoop.security.UserGroupInformation;
public class KerborsedJDBCSample {
public static void main(String[] args) {
String userPrincipalName = “user@REALAM.COM”;
String keytabPath = “C:/users/user/user.keytab”;
String jdbcURL = “jdbc:hive2://{hostName}:{port}/{databaseName}”;
String hivePrinicipal = “principal=hive/{hostName}@{releam}”;
Boolean isKerberosed = true;
String kdcHost = “kdc.host.com”;
String hiveHost = “hive.host.com”;
String hiveDatabase = “testdb”;
String hiveDriverClass = “org.apache.hive.jdbc.HiveDriver”;
String hiveUserName = “user”;
String hivePassword = “adasdas”;
Integer hivePort = 10000;
String releam = “REALAM.COM”;
String winUtilHome = “C:\\winutils\\”;
String query=”select * from temptable limit 10″;
jdbcSample(userPrincipalName, keytabPath, jdbcURL, hivePrinicipal, isKerberosed, kdcHost, hiveHost,hiveDatabase, hiveDriverClass, hiveUserName, hivePassword, hivePort, releam, winUtilHome, query);
}
private static void jdbcSample(String userPrincipalName, String keytabPath, String jdbcURL, String hivePrinicipal,
Boolean isKerberosed, String kdcHost, String hiveHost, String hiveDatabase, String hiveDriverClass,
String hiveUserName, String hivePassword, Integer hivePort, String releam, String winUtilHome,
String query) {
if (isKerberosed) {
System.setProperty(“hadoop.home.dir”, winUtilHome);
System.setProperty(“java.security.krb5.realm”, releam);
System.setProperty(“java.security.krb5.kdc”, kdcHost);
jdbcURL = jdbcURL + “;” + hivePrinicipal;
loginViaKeyTab(userPrincipalName, keytabPath);
}
jdbcURL = jdbcURL.replaceAll(“\\{hostName\\}”, hiveHost).replaceAll(“\\{port\\}”, “” + hivePort)
.replaceAll(“\\{databaseName\\}”, hiveDatabase).replaceAll(“\\{releam\\}”, releam);
Connection connection=null;
Statement statement=null;
ResultSet rs=null;
try {
Class.forName(hiveDriverClass);
connection = DriverManager.getConnection(jdbcURL, hiveUserName, hivePassword);
statement = connection.createStatement();
rs = statement.executeQuery(query);
ResultSetMetaData rsmd = rs.getMetaData();
int columnsNumber = rsmd.getColumnCount();
while (rs.next()) {
for(int i = 1 ; i <= columnsNumber; i++){
System.out.print(rs.getString(i) + ” “);
}
System.out.println();
}
} catch (Exception e) {
// TODO Auto-generated catch block
e.printStackTrace();
}finally {
try {
rs.close();
statement.close();
connection.close();
} catch (SQLException e) {
// TODO Auto-generated catch block
e.printStackTrace();
}
}
}
public static void loginViaKeyTab(String principalName, String keytabPath) {
try {
Configuration conf = new Configuration();
conf.set(“hadoop.security.authentication”, “Kerberos”);
UserGroupInformation.setConfiguration(conf);
UserGroupInformation.loginUserFromKeytab(principalName, keytabPath);
} catch (Exception e) {
e.printStackTrace();
}
}
}